On the 3rd of January 2009, under the pseudonym Satoshi Nakamoto (until today still unverified), a computer programmer or group of programmers launched a peer-to-peer digital cash system based on its whitepaper published in October 2008 on novel blockchain technology. This was the Bitcoin network.
In this article, we will explain simply what the Bitcoin Whitepaper is talking about technology-wise and what it means for users of financial systems as a revolution in payment.
Key Takeaways:
- Bitcoin, as lined out in the whitepaper, is a trustless digital cash system wherein a user does not need to get to know and come to trust payers and payees to not cheat them, and is not ambiguous about whether a payment has or has not been made.
- Bitcoin is coded to reject fraudulent transactions and to make attacking ownership by digital means extremely difficult.
- All ownership of Bitcoin currency is secured by a subset of participants who choose to engage in mining which rewards them with more Bitcoin, incentivising contribution to security and persuading malicious actors to follow suit instead of attacking.
- Becoming a user of Bitcoin for transacting does not require the disclosure of any personal information. It only requires the user to secure their private key to their Bitcoin address.
The Bitcoin Whitepaper
The Bitcoin Whitepaper laid the foundation for a revolution in payment technology, challenging the paradigm of the traditional trust-based financial model just as the 2008 global financial crisis hit economies around the world. It described succinctly in simple language the flaws of the traditional model that the public has come to accept as unavoidable, how a trustless digital cash system could circumvent these flaws and the technological concepts that would go into such a system.
The paper contains an abstract and a further twelve parts:
- Introduction
- Transactions
- Timestamp Server
- Proof-of-Work
- Network
- Incentive
- Reclaiming Disk Space
- Simplified Payment Verification
- Combining and Splitting Value
- Privacy
- Calculations
- Conclusion
The Flaws Of Trust-Based Finance
The Bitcoin Whitepaper begins with a critique of the traditional financial system.
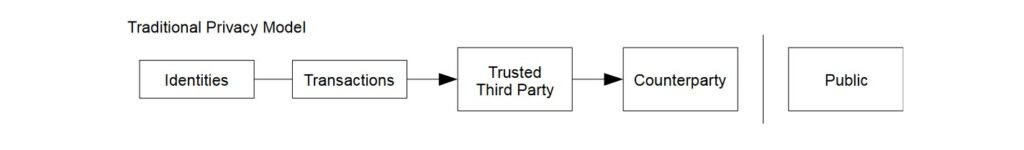
In the traditional trust-based financial system, outside of transacting in person with a physical piece of currency, transactions between two parties are arbitrated by a neutral third party; a financial institution like a bank or payment provider.
However, this system relies on trust. Having a trusted third party is based on the premise that the two transacting parties distrust each other but will be able to agree on a common third party they both trust, who has to provide a fair payment service and maintain excellent credentials.
Having to trust a third party spurs various pressures. Third parties will come under increasing scrutiny and government regulation as payers and payees demand more trust in their neutral third parties. This adds cost to payment services as trusted third parties constantly have to strive to maintain compliance. In similar fashion, payers and payees will be increasingly compelled by third parties to submit more information than required in order to use payment services for third parties to avoid serving unscrupulous actors intending to defraud others and meet compliance standards, raising issues of data privacy and further raising cost.
On an operational level, financial institutions acting as third parties cannot make their transactions truly non-reversible — locking in ownership of funds after transaction has happened — in case of disputes. Mediation of disputes also adds cost to payment services charged as fees to payer and/or payee. Small, casual transactions become hard to serve as fees are too hefty for the payer/payee or too unappealing for third parties, placing a minimum on transaction amount. When payments are reversible while goods and services once delivered are not, the market, knowing that large sums paid to them can be reversed, will become increasingly wary and demand more trust and sensitive information from buyers.
To top it off, a certain amount of fraud taking place has come to be seen as an inevitable occurrence and has been accepted as a cost of doing business.
“These costs and payment uncertainties can be avoided in person by using physical currency, but no mechanism exists to make payments over a communications channel without a trusted party.”
~ Bitcoin Whitepaper (1. Introduction)
As such, the traditional trust-based system put itself on a path of ever-increasing trust requirements, government interference in business, and costly balancing acts between compliance and data privacy.
What Is Bitcoin?
Bitcoin is a digital peer-to-peer digital cash system that prevents double-spending while simultaneously eliminating the need for a trusted third party.
“What is needed is an electronic payment system based on cryptographic proof instead of trust, allowing any two willing parties to transact directly with each other without the need for a trusted third party.”
~ Bitcoin Whitepaper (1. Introduction)
What Is Double-Spending?
The whitepaper aptly uses the term “double-spending” to characterise fraud. It refers to the intention of a defrauder to spend an amount of currency on hand more than once at different merchants in order to obtain unscrupulously goods and services worth that amount of currency multiple times.
Since fraud is impossible with in-person payments and physical cash, Bitcoin as a digital cash system emulates the locking-in of transactions non-reversibly once a transaction is declared and a payer will be unable to take back ownership of spent currency from the payee. This removes the need for a trusted third party, its transaction services, cost of mediation, and all the disadvantages that entail.
Following that, Bitcoin’s code is structured to recognise the owners of the currency and to protect their ownership of it. Various incentives that reward honest behaviour and protection of ownership in participants and disincentives that deter potential attackers from double-spending are built into the system.
How Does Bitcoin Prevent Fraud?
Bitcoin prevents fraud as we know it in the traditional financial system by ensuring that double-spending does not happen. In essence, a given sum of currency can only be spent once.
Through its code, transactions are timestamped when they are signed by the payer and broadcast to the network (more on signing and broadcasting below). Only the first transaction of the given currency sum counts toward spending. Technology wise, this makes it impossible a potential defrauder from spending the same currency twice (even in quick succession) in order to cheat the system while making it clear to the recipient that payment is still pending.
This realignment of what it means to transact digitally essentially forms the basis of a trustless system wherein payers and payees do not have to evaluate the trustworthiness of other parties in order to transact and do business. Once the merchant receives a transaction that has been confirmed and recorded in the ledger, it belongs to him and cannot be rerouted back to the payer.
To contrast the trustless system, the Bitcoin Whitepaper describes what a trust-based currency system would have to be if it was to prevent double-spending:
“A common solution is to introduce a trusted central authority, or mint, that checks every transaction for double spending. After each transaction, the coin must be returned to the mint to issue a new coin, and only coins issued directly from the mint are trusted not to be double-spent. The problem with this solution is that the fate of the entire money system depends on the company running the mint, with every transaction having to go through them, just like a bank.”
~ Bitcoin Whitepaper (2. Transactions)
Recognising Currency Ownership
Owners of Bitcoin have both a set of private and public keys. In order to send currency, an owner digitally signs the hash of the transaction that sent the currency to his wallet address and the public key of the next owner with his private key. A sum of Bitcoin is thus a chain of signed transactions wherein the latest transaction is added to the end of the chain once it is signed. A sum of bitcoin can be likened to a Russian doll set where there is a series of smaller dolls contained within the larger, current one.
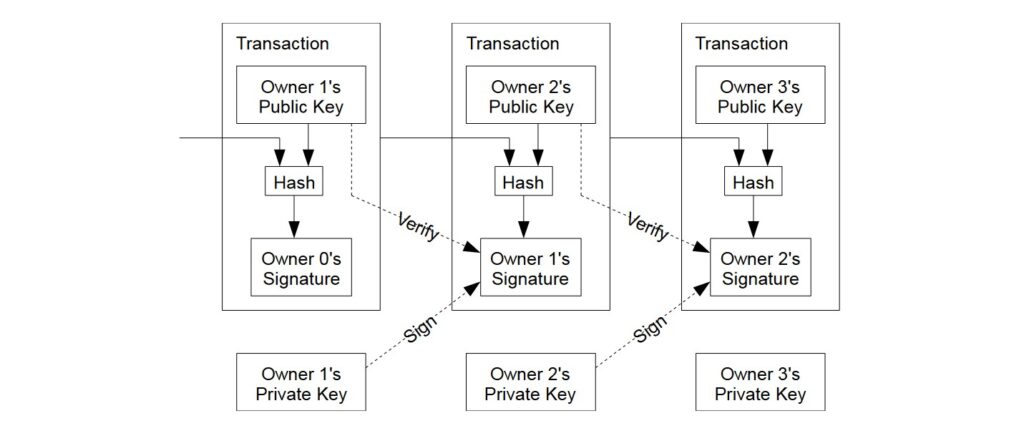

However, only being able to see the chain of ownership would not inherently allow the current owner to verify if any of the previous owners have double-spent the currency in question.
The whitepaper’s solution to this? All transactions, once signed, will be broadcasted to and stored across the network. Nodes, essentially computers owned by individuals and entities using Bitcoin that have installed the software to store broadcasted transactions, store them for the purpose of establishing a single history of timestamped transactions (a blockchain). Nodes that have gone offline for some time will request for the latest transactional history to update itself.
“In the mint based model, the mint was aware of all transactions and decided which arrived first. To accomplish this without a trusted party, transactions must be publicly announced, and we need a system for participants to agree on a single history of the order in which they were received. The payee needs proof that at the time of each transaction, the majority of nodes agreed it was the first received.”
~ Bitcoin Whitepaper (2. Transactions)
This decentralisation also vastly increases the resilience of the Bitcoin digital cash system to technical failure as every node, online and offline, has to be wiped out at the same time to truly lose every copy of the single history and every record of currency ownership.
Protecting Currency Ownership
Ownership of currency has to be recognised by the majority of the Bitcoin network’s nodes, just as the deed of a house has to be recognised by the government and the public; and a government requires work and budget to run.
In forming the single history where every transaction is signed with the hash of the previous transaction, the Bitcoin Whitepaper outlines a certain amount of work to be put in to affirm that a transaction is valid and the new owner of the currency is recognised, called the Proof-of-Work system. The Bitcoin Whitepaper starts to get technical on proof-of-work, but the key points are as follows:
- Broadcasted transactions are aggregated into blocks by nodes
- Each node tries to solve a computational puzzle involving hashes by expending their computational (CPU) power
- The block of a node that successfully solves their puzzle will be added on to the end of a chain of previous blocks (the blockchain)
- The node that has their block added to the blockchain will be rewarded with Bitcoin (incentive) and their hash is recorded on their block as proof of their work (Proof-of-Work)
- Puzzle difficulty is adjusted algorithmically so that it will take about 10 minutes to add a new block to the blockchain
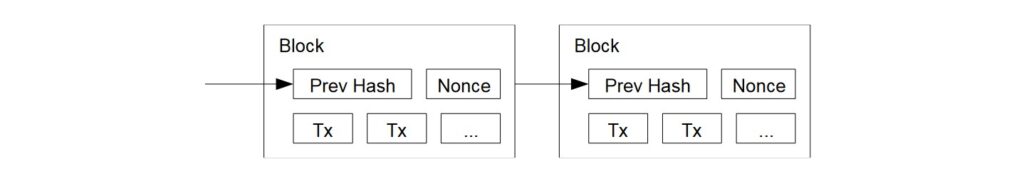
Proof-of-work also solves the issue of deciding what the majority of nodes agree upon as the single history of transactions that recognises ownership of currency:
“The proof-of-work also solves the problem of determining representation in majority decision making. If the majority were based on one-IP-address-one-vote, it could be subverted by anyone able to allocate many IPs. Proof-of-work is essentially one-CPU-one-vote. The majority
~ Bitcoin Whitepaper (4. Proof-of-Work)
decision is represented by the longest chain, which has the greatest proof-of-work effort invested in it.”
Deterring Attackers
Nodes always consider the longest chain to be the correct one and will keep working to extend it. As long as a majority of CPU power is held by honest nodes (‘honest’ meaning to abide by how Bitcoin operates), an attacker intending to cheat the system cannot change the ownership of any amount of currency as he would fail to create a blockchain that surpasses the length of and replaces the honest chain.
“To modify a past block, an attacker would have to redo the proof-of-work of the block and all blocks after it and then catch up with and surpass the work of the honest nodes.”
“If a majority of CPU power is controlled by honest nodes, the honest chain will grow the fastest and outpace any competing chains.”
~ Bitcoin Whitepaper (4. Proof-of-Work)
To illustrate difficulty an attacker would experience if they were to try to by replace the honest chain, the whitepaper goes through a series of calculations with the following conclusions:
- If a majority (>50%) of CPU power is held by honest nodes, the probability of an attack being successful is 0.
- A sender attempting to defraud would want to make the recipient believe he has been paid before rerouting the amount back to himself.
- If an attacker makes up 10% of CPU power and attacks 50 minutes after transaction, his probability of success is still 0.1%
- If an attacker makes up 30% of CPU power and attacks 4 hours after transaction, his probability of success is still 0.1%
- If an attacker makes up 45% of CPU power and attacks 56.6 hours after transaction, his probability of success is still 0.1%
- If a majority (>50%) of CPU power is held by an attacker, the probability of an attack being successful is 1.
Finally, assuming that an attacker is able to muster more CPU power than all the honest nodes and overpower them, replacing the honest chain with his own, the implications of a successful attack on Bitcoin are still themselves deterrents:
“We consider the scenario of an attacker trying to generate an alternate chain faster than the honest chain. Even if this is accomplished, it does not throw the system open to arbitrary changes, such as creating value out of thin air or taking money that never belonged to the attacker.”
“Nodes are not going to accept an invalid transaction as payment, and honest nodes will never accept a block containing them. An attacker can only try to change one of his own transactions to take back money he recently spent.”
~ Bitcoin Whitepaper (11. Calculations)
For such a colossal effort, if ever successful, the potential returns are tiny, not to mention that the honest nodes and the network as a whole would abandon their positions in Bitcoin quickly and move on to set up an improved alternative to Bitcoin. A successful attacker would have managed to retake currency that no one will accept anymore. These are easily the largest deterrents to any attacker out for fraudulent gain.
Incentivising Security
Incentives are present in Bitcoin for nodes to take part in securing ownership of Bitcoin. By contributing their CPU power and electricity to solving hash puzzles, nodes are rewarded with Bitcoin upon successfully adding blocks of validated transactions and lengthening the established blockchain. This process has been called mining, named after the act of expending resources and energy to mine for gold to be used as money.
This incentive will also dissuade attackers from trying to compete with the established honest chain with a chain of their own. By making securing of ownership with CPU power rewarding, an attacker with a competently large amount of CPU power to overpower the rest of the network is forced to choose between exerting that much force to defraud and being rewarded handsomely for turning his massive CPU power toward mining, in the process securing the ownership of bitcoin owners.
“He ought to find it more profitable to play by the rules, such rules that favour him with more new coins than everyone else combined, than to undermine the system and the validity of his own wealth.”
~ Bitcoin Whitepaper (6. Incentive)
Privacy of Bitcoin Users
Bitcoin’s handling of privacy is superior compared to that of the traditional trust-based system. Its code is structured for privacy while protecting Bitcoin owners at the same time.
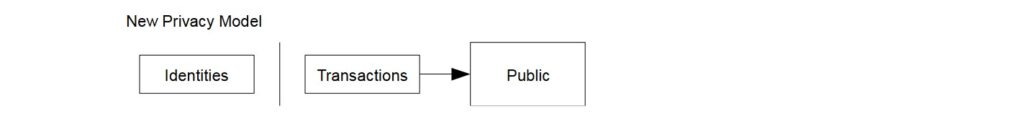
Bitcoin’s trustless model does away with a neutral third party, instead operating on code that rejects double-spending and does not favour any party nor requires their personal information in order to transact.
When trust is not required, neither are third parties. Every party, whether payer or payee, only needs to secure their private key from others and communicate their public key to others to receive payment.
Because only public keys are used in transacting, every transaction can be open to the public for scrutiny and recording, protecting personal information while bolstering the protection of ownership.
The traditional trust-based system, on the other hand, requires that payers and payees reveal a lot about themselves to their third party and to their governments in order to be trusted so that they may receive payment services.
Conclusion
Bitcoin is a peer-to-peer digital cash system for trustless transacting without third parties, and its whitepaper comes full-circle in describing how to achieve that.
By using Proof-of-Work, it records a single history of transactions that lock in ownership of Bitcoin currency non-reversibly. It is highly safe against attacks as long as honest nodes control the majority of computing power. There are many deterrents put in place against attackers, both technological and consequential, and incentives for owners of large computing power to abide by the rules of Bitcoin instead of violating them, and rewards for contributing to ownership security across the network. The use of hashes, private keys, and public keys contribute to the anonymity of currency owners while providing sufficient information about whether another address has double-spent and thus about whether the owner of that address might be untrustworthy.